Konfigurasi Htaccess Untuk Mengamankan Memperkuat Wordpress
Konfigurasi htaccess memperkuat wordpress
Halo sobat, kali ini saya akan berbagi tips konfigurasi htaccess memperkuat wordpress. Apakah Anda ingin punya website dengan skor yang bagus seperti gambar berikut ini? Jika ya, yuk lanjut baca artikel ini sampai tuntas
Maka, cara untuk memperkuat wordpress dengan menambahkan beberapa baris pada file .htaccess. Semoga bermanfaat
Akses Cpanel
Pertama, hal yang harus kita lakukan untuk konfigurasi htaccess memperkuat wordpress adalah membuka control panel cpanel. Kedua, masuk modul File Manager, dan menuju folder website kita berada. Umum nya, untuk website utama ada di folder public_html, namun jika website kita sebagai addon domain, maka folder nya sesuai dengan nama domain.
Kemudian, klik kanan pada file .htaccess dan pilih edit. Jika Anda tidak melihat file tersebut, maka kita harus ubah dulu settings pada file manager, karena file .htaccess itu termasuk hidden file, bisa kita lihat dari nama file nya berawalan titik .htaccess.
Edit File Konfigurasi htaccess memperkuat wordpress
Seterusnya, perlu Anda ingat bahwa di htacess itu ada kode-kode per block, jadi jangan menimpa kode lain nya. Contoh kode blok yang umum adalah seperti ini :
# BEGIN WordPress
# The directives (lines) between "BEGIN WordPress" and "END WordPress" are
# dynamically generated, and should only be modified via WordPress filters.
# Any changes to the directives between these markers will be overwritten.
RewriteEngine On
RewriteRule .* - [E=HTTP_AUTHORIZATION:%{HTTP:Authorization}]
RewriteBase /
RewriteRule ^index\.php$ - [L]
RewriteCond %{REQUEST_FILENAME} !-f
RewriteCond %{REQUEST_FILENAME} !-d
RewriteRule . /index.php [L]
# END WordPress
Jadi, jangan memasukkan kode baru diantara block BEGIN WordPress dan END WordPress. Langkah selanjutnya adalah mengisi beberapa baris berikut ini.
Menambahkan security header
# Start Security Headers
<IfModule mod_headers.c>
# X-Frame-Options
Header always set X-Frame-Options "SAMEORIGIN"
# X-XSS-Protection
Header always set X-XSS-Protection "1; mode=block"
# X-Content-Type-Options
Header always set X-Content-Type-Options nosniff
# Referrer-Policy
Header always set Referrer-Policy "strict-origin"
# Content-Security-Policy
# Header set Content-Security-Policy-Report-Only default-src 'self' 'unsafe-inline' https://fonts.googleapis.com; script-src 'self' 'unsafe-inline' https://maps.googleapis.com; frame-ancestors 'self'; block-all-mixed-content; form-action 'self'; font-src 'self' [URL]https://fonts.gstatic.com[/URL] data:; img-src 'self' https://secure.gravatar.com data:;
Header set Content-Security-Policy default-src 'self' 'unsafe-inline' https://fonts.googleapis.com; script-src 'self' 'unsafe-inline' https://maps.googleapis.com; frame-ancestors 'self'; block-all-mixed-content; form-action 'self'; font-src 'self' [URL]https://fonts.gstatic.com[/URL] data:; img-src 'self' https://secure.gravatar.com data:;
# Feature Policy
Header set Feature-Policy "geolocation 'none'; midi 'none'; camera 'none'; usb 'none'; magnetometer 'none'; accelerometer 'none'; vr 'none'; speaker 'none'; ambient-light-sensor 'none'; gyroscope 'none'; microphone 'none'"
# Unset headers revealing versions strings
Header unset X-Powered-By
Header unset X-Pingback
Header unset SERVER
# Disable Entity Tag Header
Header unset ETag
FileETag None
#Set secure cookies
Header always edit Set-Cookie ^(.*)$ $1;HttpOnly;Secure;SameSite=Strict
# Set Keep Alive Header
Header set Connection keep-alive
# Instructs the proxy to store both a compressed and uncompressed version of the resource
<FilesMatch ".(js|css|xml|gz|html|woff|woff2|ttf)$">
Header append Vary: Accept-Encoding
</FilesMatch>
</IfModule>
# End Security Headers
Tambahan firewall lain nya seperti 6G Firewall dll
Lalu, kita tambahkan firewall nya. Selain itu, beberapa baris juga kita tambahkan. Namun, kita juga harus hati-hati dalam mengubah htaccess. Meskipun begitu, mari kita lanjutkan.
# Protect number of important WordPress and web server files such as config, ini and log files (this also includes wp-config.php etc)
<FilesMatch "^(wp-config\.php|wp-mail\.php|repair\.php|xmlrpc\.php|php\.ini|php5\.ini|install\.php|php\.info|readme\.html|bb-config\.php|\.htaccess|\.htpasswd|error_log|error\.log|PHP_errors\.log|\.svn|\.log|\.bak|wlwmanifest.xml|\..*)">
Require all denied
# Prevent WordPress usernames from enumerating
RewriteCond %{REQUEST_URI} !^/wp-admin [NC]
RewriteCond %{QUERY_STRING} ^author=\d+ [NC,OR]
RewriteCond %{QUERY_STRING} ^author=\{num [NC]
RewriteRule ^(.*)$ - [F,L]
# Block access to WordPress login page from malformed requests
RewriteCond %{REQUEST_METHOD} POST
RewriteCond %{REQUEST_URI} ^(.*)?wp-login\.php(.*)$ [NC,OR]
RewriteCond %{REQUEST_URI} ^(.*)?wp-admin?(/)$ [NC]
RewriteCond %{HTTP_REFERER} !(.*)domain\.co(.*) [NC,OR]
RewriteCond %{HTTP_USER_AGENT} ^-?$ [OR]
RewriteCond %{HTTP_USER_AGENT} ^.*(jorgee|morfeusfirefox\/34.0|mozilla\/4.0|firefox\/40.1).* [NC]
RewriteRule ^(.*)$ - [F,L]
# Restrict access to WordPress PHP files from plugin and theme directories
RewriteCond %{REQUEST_URI} ^(.*)?wp-content/plugins/(.*\.php)$ [NC]
RewriteRule ^(.*)$ - [F,L]
RewriteCond %{REQUEST_URI} ^(.*)?wp-content/themes/(.*\.php)$ [NC]
RewriteRule ^(.*)$ - [F,L]
# Block access to WordPress includes folder
RewriteCond %{REQUEST_URI} ^(.*)?wp-admin/includes/(.*\.php)$ [NC, OR]
RewriteCond %{REQUEST_URI} ^(.*)?wp-includes/js/tinymce/langs/(.*\.php)$ [NC, OR]
RewriteCond %{REQUEST_URI} ^(.*)?wp-includes/theme-compat/(.*\.php)$ [NC]
RewriteRule ^(.*)$ - [F,L]
<If "%{REQUEST_URI} =~ m#^(.*)?/wp-content/uploads/(.*\.txt)#">
Require all denied
# Block Nuisance Requests
# https://perishablepress.com/block-nuisance-requests
# RedirectMatch 403 (?i)\.php\.suspected
# RedirectMatch 403 (?i)\.(git|well-known)
# RedirectMatch 403 (?i)apple-app-site-association
# RedirectMatch 403 (?i)/autodiscover/autodiscover.xml
RewriteCond %{REQUEST_URI} ^(.*)?(\.php\.suspected|\.well-known|\.git|apple|autodiscover)(.*)$ [NC]
RewriteRule ^(.*)$ - [F,L]
# Blocking the »ReallyLongRequest« Bandit
# https://perishablepress.com/blocking-reallylongrequest-bandit/
RewriteCond %{REQUEST_METHOD} .* [NC]
RewriteCond %{THE_REQUEST} (YesThisIsAReallyLongRequest|ScanningForResearchPurpose) [NC,OR]
RewriteCond %{QUERY_STRING} (YesThisIsAReallyLongRequest|ScanningForResearchPurpose) [NC]
RewriteRule ^(.*)$ - [F,L]
# 6G:[QUERY STRING]
RewriteEngine On
RewriteCond %{QUERY_STRING} (eval\() [NC,OR]
RewriteCond %{QUERY_STRING} (127\.0\.0\.1) [NC,OR]
RewriteCond %{QUERY_STRING} ([a-z0-9]{2000,}) [NC,OR]
RewriteCond %{QUERY_STRING} (javascript:)(.*)(;) [NC,OR]
RewriteCond %{QUERY_STRING} (base64_encode)(.*)(\() [NC,OR]
RewriteCond %{QUERY_STRING} (GLOBALS|REQUEST)(=|\[|%) [NC,OR]
RewriteCond %{QUERY_STRING} (<|%3C)(.*)script(.*)(>|%3) [NC,OR]
RewriteCond %{QUERY_STRING} (\\|\.\.\.|\.\./|~|`|<|>|\|) [NC,OR]
RewriteCond %{QUERY_STRING} (boot\.ini|etc/passwd|self/environ) [NC,OR]
RewriteCond %{QUERY_STRING} (thumbs?(_editor|open)?|tim(thumb)?)\.php [NC,OR]
RewriteCond %{QUERY_STRING} (\'|\")(.*)(drop|insert|md5|select|union) [NC]
RewriteRule .* - [F]
# 6G:[REQUEST METHOD]
RewriteCond %{REQUEST_METHOD} ^(connect|debug|move|put|trace|track) [NC]
RewriteRule .* - [F]
# 6G:[REFERRER]
RewriteCond %{HTTP_REFERER} ([a-z0-9]{2000,}) [NC,OR]
RewriteCond %{HTTP_REFERER} (semalt.com|todaperfeita) [NC]
RewriteRule .* - [F]
# 6G:[REQUEST STRING]
RedirectMatch 403 (?i)([a-z0-9]{2000,})
RedirectMatch 403 (?i)(https?|ftp|php):/
RedirectMatch 403 (?i)(base64_encode)(.*)(\()
RedirectMatch 403 (?i)(=\\\'|=\\%27|/\\\'/?)\.
RedirectMatch 403 (?i)/(\$(\&)?|\*|\"|\.|,|&|&?)/?$
RedirectMatch 403 (?i)(\{0\}|\(/\(|\.\.\.|\+\+\+|\\\"\\\")
RedirectMatch 403 (?i)(~|`|<|>|:|;|,|%|\\|\{|\}|\[|\]|\|)
RedirectMatch 403 (?i)/(=|\$&|_mm|cgi-|muieblack)
RedirectMatch 403 (?i)(&pws=0|_vti_|\(null\)|\{\$itemURL\}|echo(.*)kae|etc/passwd|eval\(|self/environ)
RedirectMatch 403 (?i)\.(aspx?|bash|bak?|cfg|cgi|dll|exe|git|hg|ini|jsp|log|mdb|out|sql|svn|swp|tar|rar|rdf)$
RedirectMatch 403 (?i)/(^$|(wp-)?config|mobiquo|phpinfo|shell|sqlpatch|thumb|thumb_editor|thumbopen|timthumb|webshell)\.php
# 6G:[USER AGENT]
SetEnvIfNoCase User-Agent ([a-z0-9]{2000,}) bad_bot
SetEnvIfNoCase User-Agent (archive.org|binlar|casper|checkpriv|choppy|clshttp|cmsworld|diavol|dotbot|extract|feedfinder|flicky|g00g1e|harvest|heritrix|httrack|kmccrew|loader|miner|nikto|nutch|planetwork|postrank|purebot|pycurl|python|seekerspider|siclab|skygrid|sqlmap|sucker|turnit|vikspider|winhttp|xxxyy|youda|zmeu|zune) bad_bot
# Apache < 2.3
Order Allow,Deny
Allow from all
Deny from env=bad_bot
# Apache >= 2.3
Require all Granted
Require not env bad_bot
# END custom directives
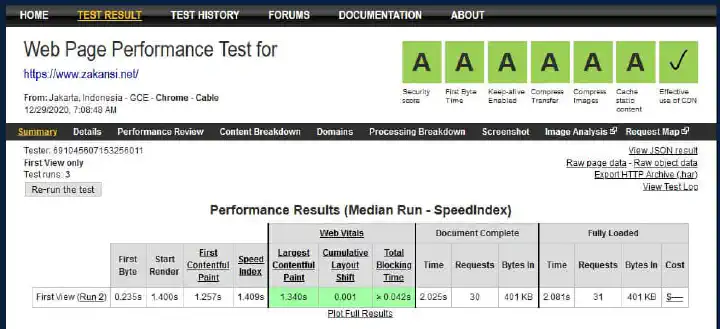
Setelah itu, Anda simpan dan lakukan test dengan menggunakan situs https://www.webpagetest.org. Selanjutnya, nanti akan terlihat tingkatan security nya, apakah nilai nya A+, A, B, C atau bahkan buruk yaitu F. Untuk website zakansi.net ini, skor nilai nya adalah A semua, dan hijau, seperti ini :

Alhasil, sekian dari saya, semoga bermanfaat. Memang, jika ada yang ingin ditanyakan, silakan tulis di komentar bawah.